Generating Pacman Keychain Master Key Takes Forever
May 15, 2015 A simple and unified api that enables developer to set, update, get and delete keys and passwords on the keyChain (supports iOS, Android, and WinPhone) - has-taiar/KeyChain.Net. Many users confirm this happening, and a fix being 'generating entropy' via running ls -R / in another terminal or by connecting and moving around a mouse while pacman-key -init is hanging. This input should be automated or it should be surfaced to the user that it is required.
- Master Key Korean Variety Show
- Generating Pacman Keychain Master Key Takes Forever Online
- Generating Pacman Keychain Master Key Takes Forever Download
- Generating Pacman Keychain Master Key Takes Forever Free
- Master Key Vietsub
Nov 04, 2011 Running pacman-key I get youri@slavluv $ sudo pacman-key -init gpg: Generating pacman keychain master key. Not enough random bytes available. Please do some other work to give the OS a chance to collect more entropy! (Need 284 more bytes). Find helpful customer reviews and review ratings for PacMan Keychain with Sound at Amazon.com. Read honest and unbiased product reviews from our users. Oct 27, 2016 I bypassed the checking of the keys for all pacman repositories and was able to go through the whole installation. I don't really want to spend more time re-installing so I call it works-for-me. Apr 24, 2013 A short demo of our Pac-Man Keychain (with authentic arcade sounds). Pacman Pac-Man Mashems Series 1 Squishy Toy Review. Collins Key Recommended for you. Language: English.
To determine if packages are authentic, pacman uses GnuPG keys in a web of trust model. The current Master Signing Keys are found here. At least three of these Master Signing Keys are used to sign the Developer's and Trusted User's own keys. They are then used to sign their packages. Each user also has a unique PGP key, which is generated when you configure pacman-key. It is this web of trust that links the user's key to the master keys.
Examples of webs of trust:
- Custom packages: Packages made and signed with a local key.
- Unofficial packages: Packages made and signed by a developer. Then, a local key was used to sign the developer's key.
- Official packages: Packages made and signed by a developer. The developer's key was signed by the Arch Linux master keys. You used your key to sign the master keys, and you trust them to vouch for developers.
- 1Setup
- 2Managing the keyring
- 3Troubleshooting
Setup
Configuring pacman
The SigLevel option in /etc/pacman.conf determines the level of trust required to install a package. For a detailed explanation of SigLevel see the pacman.conf man page and the file comments. One can set signature checking globally or per repository. If SigLevel is set globally in the [options] section, all packages will then require signing. Any packages you build will then need to be signed using makepkg.
Required is set then DatabaseOptional should also be set.The default configuration will only support the installation of packages signed by trusted keys:
TrustedOnly is a default compiled-in pacman parameter. The default configuration is identical to using the global option of:
The above can be achieved too on a repository level further below in the configuration, e.g.:
You can find more information on the BeginnersHelp page. PCGAME FIXESRise Of Nations: Thrones And Patriotsfor related No-CD & No-DVD PatchNo-CD & No-DVD Patch troubleshooting: The most common problem gettinga No-CD/No-DVD patch to work is ensuring that the No-CD/No-DVDpatch matches you're game version, because the games exe ischanged when a patch update is applied previous versions won'twork.If its an older game you areplaying and you are running Windows 7 or Windows 8 it may not work,if you right click the.exe file and choose Properties andthen Compatibility you can change this to run in Windows 98/Windows 2000 etc. 
explicitly adds signature checking for the packages of the repository, but does not require the database to be signed. Optional here would turn off a global Required for this repository
Generating Your SSH Public Key. Many Git servers authenticate using SSH public keys. In order to provide a public key, each user in your system must generate one if they don’t already have one. This process is similar across all operating systems. First, you should check to make sure you don’t already have a key. If you don't already have an SSH key, you must generate a new SSH key. If you're unsure whether you already have an SSH key. If you have GitHub Desktop installed, you can use it to clone repositories and not deal with SSH keys. It also comes with the Git Bash tool, which is the preferred way of running git commands on Windows. Mar 25, 2010 Now you need to generate a public SSH key to authenticate yourself. If you installed TortoiseGit, you should have Puttygen installed too. Open it and generate a private and a public key. Save the public key and the private key with the same filename, the only difference is that the private key should have a.ppk file extension. Windows git SSH authentication to GitHub. Follow @vlad. If you don’t have a SSH public/private key pair you can generate it using the puttygen utility. KitsPuttyplink.exe -v git@github.com Looking up host 'github.com' Connecting to 192.30.252.129 port 22 Server version: SSH-2.0-libssh-0.6.0 Using SSH protocol version 2 We claim. Go to Windows Start menu → All Programs → PuTTY → PuTTYgen. Creating a new key pair for authentication. To create a new key pair, select the type of key to generate from the bottom of the screen (using SSH-2 RSA with 2048 bit key size is good for most people; another good well-known alternative is. 
TrustAll option exists for debugging purposes and makes it very easy to trust keys that have not been verified. You should use TrustedOnly for all official repositories.Initializing the keyring
To initialize the pacman keyring run:
Initializing the keyring requires entropy. To generate entropy, move your mouse around, press random characters on the keyboard, or run some disk-based activity (for example in another console running ls -R / or find / -name foo or dd if=/dev/sda8 of=/dev/tty7). If your system does not already have sufficient entropy, this step may take hours; if you actively generate entropy, it will complete much more quickly.
The randomness created is used to initialize the keyring (/etc/pacman.d/gnupg) and the GPG signing key of your system.
pacman-key --init on computer that does not generate much entropy (e.g. a headless server), key generation may take a very long time. To generate pseudo-entropy, install either haveged or rng-tools on the target machine and start the corresponding service before running pacman-key --init.Managing the keyring
Verifying the master keys
The initial setup of keys is achieved using:
Take time to verify the Master Signing Keys when prompted as these are used to co-sign (and therefore trust) all other packager's keys.
PGP keys are too large (2048 bits or more) for humans to work with, so they are usually hashed to create a 40-hex-digit fingerprint which can be used to check by hand that two keys are the same. The last eight digits of the fingerprint serve as a name for the key known as the '(short) key ID' (the last sixteen digits of the fingerprint would be the 'long key ID').
Adding developer keys
The official developer and Trusted Users(TU) keys are signed by the master keys, so you do not need to use pacman-key to sign them yourself. Whenever pacman encounters a key it does not recognize, it will prompt to download it from a keyserver configured in /etc/pacman.d/gnupg/gpg.conf (or by using the --keyserver option on the command line). Wikipedia maintains a list of keyservers.
Once you have downloaded a developer key, you will not have to download it again, and it can be used to verify any other packages signed by that developer.
pacman-key --refresh-keys (as root). While doing --refresh-keys, your local key will also be looked up on the remote keyserver, and you will receive a message about it being not found. This is nothing to be concerned about.Adding unofficial keys
This method can be utilized to add a key to the pacman keyring, or to enable signed unofficial user repositories.
First, get the key ID (keyid) from its owner. Then add it to the keyring using one of the two methods:
- If the key is found on a keyserver, import it with:
- If otherwise a link to a keyfile is provided, download it and then run:
It is recommended to verify the fingerprint, as with any master key or any other key you are going to sign:
Finally, you must locally sign the imported key:
You now trust this key to sign packages.
Debugging with gpg
For debugging purposes, you can access pacman's keyring directly with gpg, e.g.:
Troubleshooting
This article or section needs language, wiki syntax or style improvements. See Help:Style for reference.
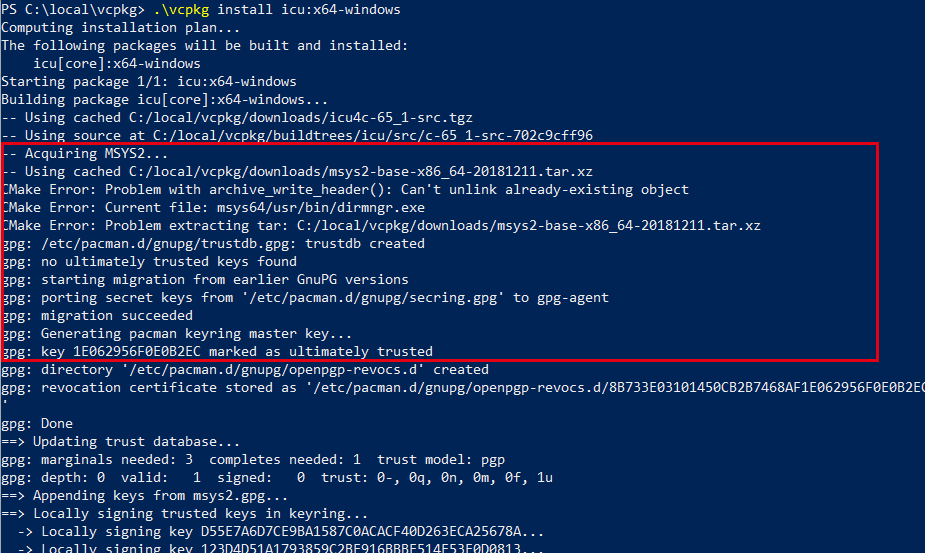
Cannot import keys
There are multiple possible sources of this problem:
- An outdated archlinux-keyring package.
- Incorrect date.
- Your ISP blocked the port used to import PGP keys.
- Your pacman cache contains copy of unsigned packages from previous attempts.
dirmngris not correctly configured
You might be stuck because of outdated archlinux-keyring package when doing an upgrade synchronization. Try if upgrading the system can fix it first.
This article or section needs language, wiki syntax or style improvements. See Help:Style for reference.
If you are still having issues, make sure the following file exists /root/.gnupg/dirmngr_ldapservers.conf and that you can successfully run # dirmngr. Create an empty file if it doesn't and run # dirmngr again.
If it does not help and your date is correct, you could try to switch to the MIT keyserver, which provides an alternate port. To do this, edit /etc/pacman.d/gnupg/gpg.conf and change the keyserver line to:
If even port 80 doesn't work (for example when company uses some kind of http-only 'transparent' proxy instead of routing, following could work:
If you have IPv6 disabled, gpg will fail when it found some IPv6 address. In this case try with an IPv4-only keyserver like:
If you happen to forget to run pacman-key --populate archlinux you might get some errors while importing keys.
If none of this helps, your pacman cache, located at /var/cache/pacman/pkg/ might contain unsigned packages from previous attempts. Try cleaning the cache manually or run:
which removes all cached packages that have not been installed.
Disabling signature checking
If you are not concerned about package signing, you can disable PGP signature checking completely. Edit /etc/pacman.conf and uncomment the following line under [options]:
You need to comment out any repository-specific SigLevel settings too because they override the global settings. This will result in no signature checking, which was the behavior before pacman 4. If you decide to do this, you do not need to set up a keyring with pacman-key. You can change this option later if you decide to enable package verification.
Master Key Korean Variety Show
Resetting all the keys
If you want to remove or reset all the keys installed in your system, you can remove /etc/pacman.d/gnupg folder as root and rerun pacman-key --init followed by pacman-key --populate archlinux to re-add the default keys.
Removing stale packages
If the same packages keep failing and you are sure you did all the pacman-key stuff right, try removing them like so rm /var/cache/pacman/pkg/badpackage* so that they are freshly downloaded.
This might actually be the solution if you get a message like error: linux: signature from 'Some Person <Some.Person@example.com>' is invalid or similar when upgrading (i.e. you might not be the victim of a MITM attack after all, your downloaded file was simply corrupt).
Signature is unknown trust
Sometimes when running pacman -Suy you might encounter this error:
This occurs because the packager's key used in the package package-name is not present and/or not trusted in the local pacman-key gpg database. Pacman does not seem to always be able to check if the key was received and marked as trusted before continuing. This could also be because a key has expired since it was added to your keychain.
Generating Pacman Keychain Master Key Takes Forever Online
Mitigate by:
- Refreshing your keys with
pacman-key --refresh-keys, or - manually signing the untrusted key locally, or
- resetting all the keys.
Updating keys via proxy
In order to use a proxy when updating keys the honor-http-proxy option must be set in both /etc/gnupg/dirmngr.conf and /etc/pacman.d/gnupg/dirmngr.conf. See GnuPG#Use a keyserver for more information.
honor-http-proxy option and fails, a reboot may solve the issue.See also
We will provide a package that contains a GPG keyring of the developers keys for import into the pacman keyring.
The GPG keyring for pacman is managed by pacman-key and stored in /etc/pacman.d/gnupg. This keyring is created using 'pacman-key --init', which also creates an ultimately trusted 'Pacman Keychain Master Key'. For a key to be accepted by pacman as trusted after being imported to the pacman keyring (pacman-key --add/--recv-keys), it must either be locally signed by the Pacman Keychain Master Key (pacman-key --lsign <key>), given ultimate trust (via pacman-key --edit-key <key>), or reachable from an ultimately trusted key through the PGP Web of Trust.
The Arch Linux keyring will contain all packager GPG keys along with a number (~3) of 'master' keys. A user will be required to manually verify, import and locally sign the master keys into their pacman keyring. The master keys will be well published on the Arch Linux site and across various developers websites allowing users to readily verify their authenticity. Every developer key will be signed by the master keys and so will be trusted through the web of trust.
Generating Pacman Keychain Master Key Takes Forever Download
A package will be provided that contains the Arch developers GPG keys ready for import with 'pacman-key --populate'. This package (and the files in this package) will be signed (detached) by an Arch master key (or all of them). The package contains the following files:
Generating Pacman Keychain Master Key Takes Forever Free
- /usr/share/pacman/keyrings/arch.gpg - the GPG keyring containing the developer keys (and probably the master keys)
- /usr/share/pacman/keyrings/arch-revoked.gpg - [OPTIONAL] a list of revoked keys
- /usr/share/pacman/keyrings/arch-trusted - [OPTIONAL] information about which keys need trusted to the form web of trust
For more details of the files and their format, see the PROVIDING A KEYRING FOR IMPORT section of 'man pacman-key'.
- How many Arch master keys will there be?
- Note: need at least three to establish the web of trust (by default)
- Note: should be at least one 'backup' key to replace a revoked key immediately (and thus maintain web of trust)
- Query: is the backup key published before it is needed
- Who holds the master keys?
- Who holds the revoke certificates for the master keys?
- How are the master key holders going to verify the dev keys before signing them?
- Will there be separate keyrings for Developers and Trusted Users?
- Policy for handling developer keys on resignation (where revoking is probably not immediately required)