Generate New Public Key File Ubuntu
- A good compromise between convenience and security is to generate a separate key pair for each service or connection you want to use, adding a passphrase only for critical services. If you suspect a key has been compromised, simply generate a new pair for that service and remove the less secure key.
- Generate a 2048 bit RSA Key. You can generate a public and private RSA key pair like this. You need to next extract the public key file. You will use this, for instance, on your web server to encrypt content so that it can only be read with the private key. Export the RSA Public Key to a File.
- Crt and key files represent both parts of a certificate, key being the private key to the certificate and crt being the signed certificate. It's only one of the ways to generate certs, another way would be having both inside a pem file or another in a p12 container.
- Nov 10, 2011 4. Your public and private SSH key should now be generated. Open the file manager and navigate to the.ssh directory. You should see two files: idrsa and idrsa.pub. Upload the idrsa.pub file to the home folder of your remote host (assuming your remote host is running Linux as well).
- How to add Windows SSH key file to Ubuntu 16.04? Ask Question Asked 3 years, 7 months ago. I know I can create new ssh keys but that defeats the purpose of what I am trying to do. How do I configure Ubuntu 16.04 server for root public key ssh.
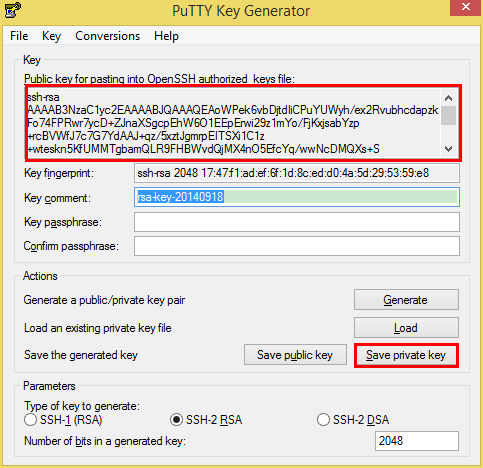
Save the public and private keys by clicking the Save public key and Save private key buttons. From the Public key for pasting into OpenSSH authorizedkeys file field at the top of the window, copy all the text (starting with ssh-rsa ) to your clipboard by pressing Ctrl-C. Create a key pair for the new user account. Create a key pair, or use an existing one. If you add the newuser to an Ubuntu instance. Shell session that is running under the context of the new user account to confirm that you have permission to add the public key to the.ssh/authorizedkeys file.
While Encrypting a File with a Password from the Command Line using OpenSSLis very useful in its own right, the real power of the OpenSSL library is itsability to support the use of public key cryptograph for encrypting orvalidating data in an unattended manner (where the password is not required toencrypt) is done with public keys.
The Commands to Run
Generate a 2048 bit RSA Key
You can generate a public and private RSA key pair like this:
openssl genrsa -des3 -out private.pem 2048
That generates a 2048-bit RSA key pair, encrypts them with a password you provideand writes them to a file. You need to next extract the public key file. You willuse this, for instance, on your web server to encrypt content so that it canonly be read with the private key.
Export the RSA Public Key to a File
This is a command that is
Generate New Public Key File Ubuntu Windows 7
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
The -pubout flag is really important. Be sure to include it.
Next open the public.pem and ensure that it starts with-----BEGIN PUBLIC KEY-----. This is how you know that this file is thepublic key of the pair and not a private key.
To check the file from the command line you can use the less command, like this:
less public.pem
Do Not Run This, it Exports the Private Key
A previous version of the post gave this example in error.
openssl rsa -in private.pem -out private_unencrypted.pem -outform PEM
The error is that the -pubout was dropped from the end of the command.That changes the meaning of the command from that of exporting the public keyto exporting the private key outside of its encrypted wrapper. Inspecting theoutput file, in this case private_unencrypted.pem clearly shows that the keyis a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----.
Visually Inspect Your Key Files
It is important to visually inspect you private and public key files to makesure that they are what you expect. OpenSSL will clearly explain the nature ofthe key block with a -----BEGIN RSA PRIVATE KEY----- or -----BEGIN PUBLIC KEY-----.
You can use less to inspect each of your two files in turn:
less private.pemto verify that it starts with a-----BEGIN RSA PRIVATE KEY-----less public.pemto verify that it starts with a-----BEGIN PUBLIC KEY-----
The next section shows a full example of what each key file should look like.
The Generated Key Files
The generated files are base64-encoded encryption keys in plain text format.If you select a password for your private key, its file will be encrypted withyour password. Be sure to remember this password or the key pair becomes useless.
Search Ubuntu For File
The private.pem file looks something like this:
The public key, public.pem, file looks like:
Protecting Your Keys
Depending on the nature of the information you will protect, it’s important tokeep the private key backed up and secret. The public key can be distributedanywhere or embedded in your web application scripts, such as in your PHP,Ruby, or other scripts. Again, backup your keys!
Remember, if the key goes away the data encrypted to it is gone. Keeping aprinted copy of the key material in a sealed envelope in a bank safety depositbox is a good way to protect important keys against loss due to fire or harddrive failure.
Oh, and one last thing.
If you, dear reader, were planning any funny business with the private key that I have just published here. Know that they were made especially for this series of blog posts. I do not use them for anything else.
Found an issue?
Rietta plans, develops, and maintains applications.
Learn more about our services or drop us your email and we'll e-mail you back.
Other Blog Articles Published by Rietta.com
Introduction
Establishing an SSH (Secure Shell) connection is essential to log in and effectively manage a remote server. Encrypted keys are a set of access credentials used to establish a secure connection.
This guide will walk you how to generate SSH keys on Ubuntu 18.04. We will also cover setting up SSH key-based authentication to connect to a remote server without requiring a password.
- A server running Ubuntu 18.04
- A user account with sudo privileges
- Access to a terminal window / command line (Ctrl-Alt-T)
If you are already running an Ubuntu 18.04 server, you can skip this step. If you are configuring your server for the first time, you may not have SSH installed.
1. Start by installing the tasksel package:
The system will first ask for confirmation before proceeding:
2. Next, use tasksel to install the ssh-server:
3. Load the SSH server service, and set it to launch at boot:
On your client system – the one you’re using to connect to the server – you need to create a pair of key codes.
To generate a pair of SSH key codes, enter the commands:
This will create a hidden directory to store your SSH keys, and modify the permissions for that directory. The ssh-keygen command creates a 2048-bit RSA key pair.
For extra security, use RSA4096:
If you’ve already generated a key pair, this will prompt to overwrite them, and those old keys will not work anymore.
Our Far Cry New Dawn Serial Key CD KEY Download hacks tool never get banned, because they’re 100% private.At Rid2690.com we are also constantly updating our Far Cry New Dawn Serial Key CD KEY Download. Far cry 4 steam key.
The system will ask you to create a passphrase as an added layer of security. Input a memorable passphrase, and press Enter.
Microsoft office 2013 personal product key generator. Use full version of MS Office 365 with Product Key for lifetime by using given crack.Microsoft Office 365 Crack is the brand name Microsoft uses for a group of subscriptions that provide productivity software and related services. This tool will support you to do offline office software by Microsoft and joined version of some online. You can enjoy all this just in the single package. Microsoft Office 365 Product Key is a complete all-in-one package of tools that support to make office full version to use its all features easily and freely. Microsoft Office is the complete product that developed by Microsoft corporation. If you want to use MS Office 365 Product Key without any problem and lifetime you have to activate it with legal license key.
This process creates two keys. One is a public key, which you can hand out to anyone – in this case, you’ll save it to the server. The other one is a private key, which you will need to keep secure. The secure private key ensures that you are the only person who can encrypt the data that is decrypted by the public key.
Step 2- Copy Public Key to the Ubuntu Server
First, get the IP address of the Ubuntu server you want to connect to.
In a terminal window, enter:
The system’s IP address is listed in the second entry:
On the client system, use the ssh-copy-id command to copy the identity information to the Ubuntu server:
Replace server_IP with the actual IP address of your server.
If this is the first time you’re connecting to the server, you may see a message that the authenticity of the host cannot be established:
Type yes and press Enter.
The system will check your client system for the id_rsa.pub key that was previously generated. Then it will prompt you to enter the password for the server user account. Type it in (the system won’t display the password), and press Enter.
The system will copy the contents of the ~/.ssh/id_rsa.pub from the client system into the ~/.ssh/authorized_keys directory of the server system.
The system should display:
If your system does not have the ssh-copy-id command, you can copy the key manually over the SSH.
Use the following command:
To log in to a remote server, input the command:
The system should not ask for a password as it is negotiating a secure connection using the SSH keys. If you used a security passphrase, you would be prompted to enter it. After you do so, you are logged in.
If this is the first time you’ve logged into the server, you may see a message similar to the one in part two. It will ask if you are sure you want to connect – type yes and press Enter.
Step 4- Disable Password Authentication
This step creates an added layer of security. If you’re the only person logging into the server, you can disable the password. The server will only accept a login with your private key to match the stored public key.
Edit the sshd_config file:
Search the file and find the PasswordAuthentication option.
Edit the file and change the value to no:
Save the file and exit, then restart the SSH service:
Verify that SSH is still working, before ending the session:
If everything works, you can close out and resume work normally.
By following the instructions in this tutorial, you have setup SSH-key-based authentication on an Ubuntu 18.04 server.
The connection is now highly secure as it uses a set of unique, encrypted SSH keys.
Next you should also read
Learn how to set up SSH key authentication on CentOS to safely communicate with remote servers. Create the…
When establishing a remote connection between a client and a server, a primary concern is ensuring a secure…
Nginx is an open-source server utility designed to work as a reverse proxy, intercepting client requests and…
In this tutorial, Find out How To Use SSH to Connect to a Remote Server in Linux or Windows. Get started with…